To benefit from SafeToOpen, you'll need the following:
• SafeToOpen Portal virtual machine in your on-prem virtual environment (such as VMware) or Cloud such as Amazon AWS and Microsoft Azure
• An email account for receiving suspicious emails (e.g., [email protected])
• An email account for sending email responses (e.g., [email protected])
* Please note that the receiving and sending email accounts can be the same
• SMTP/IMAP or Microsoft Graph account for the above account(s)
• [OPTIONAL] SafeToOpen Add-in for Outlook can be pushed for a one-click email report
Yes, you can configure SafeToOpen Email verification according to your business preferences! Within a few clicks in your settings, choose not to process or reply to certain users, users that have specific email addresses, or not from/to anyone at all.
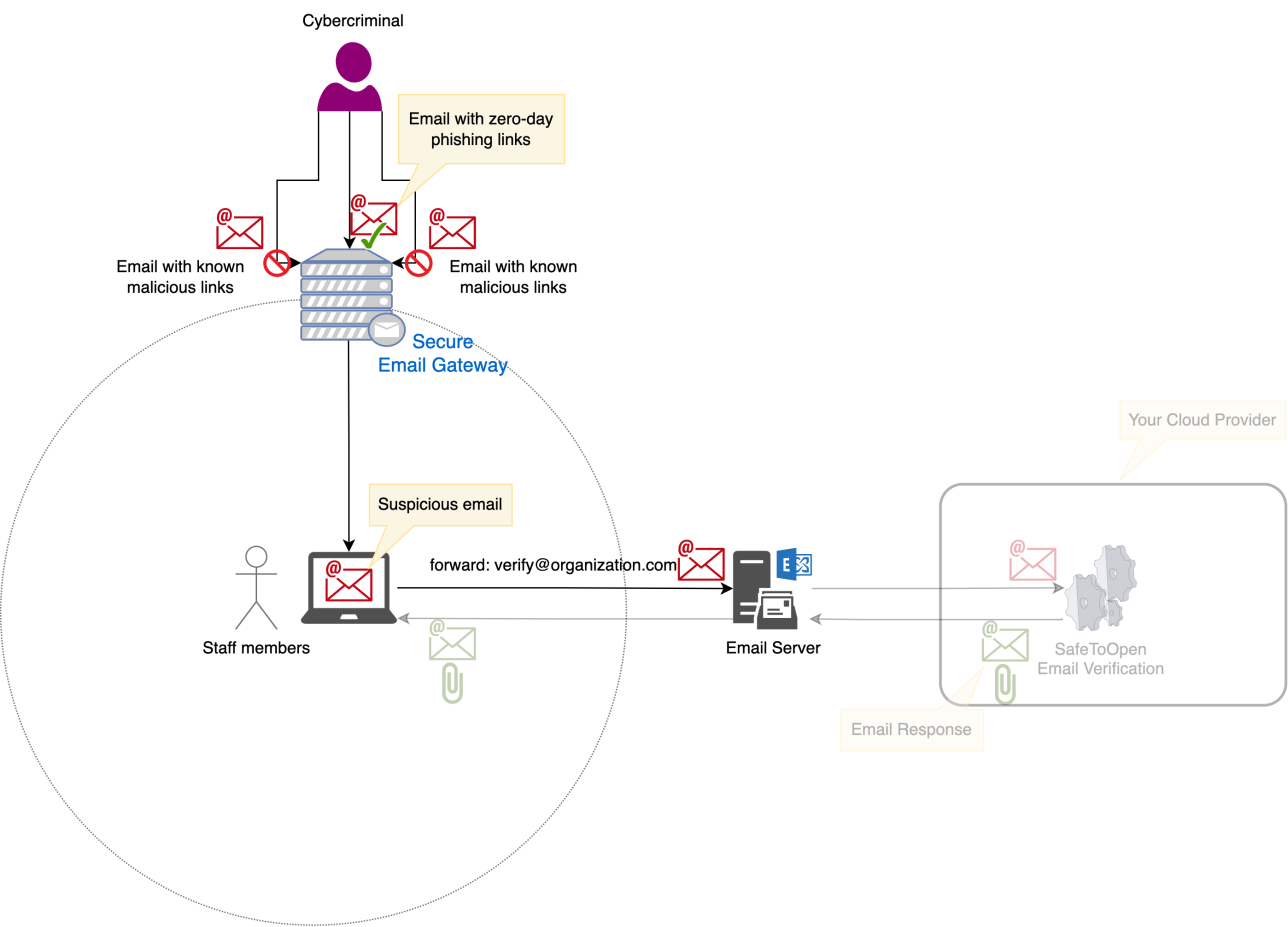
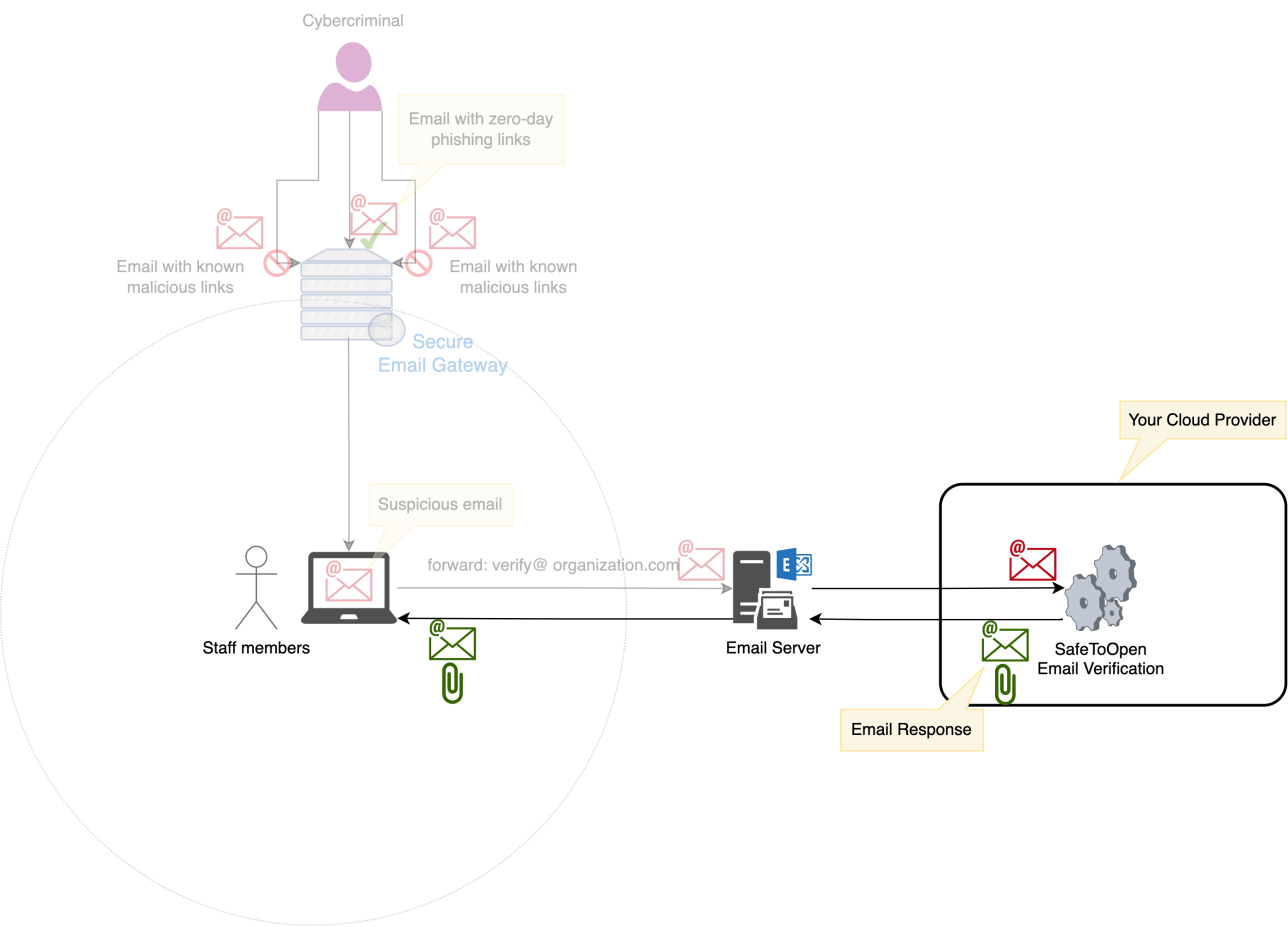
SafeToOpen Email Security is not a Secure Email Gateway (SEG) and does not process all ingress and egress emails. We're an additional layer of security assurance to the SEG, and it is effective when emails contain never-before-seen or zero-day phishing links bypassing SEGs. SafeToOpen Email Verification can identify these emails.
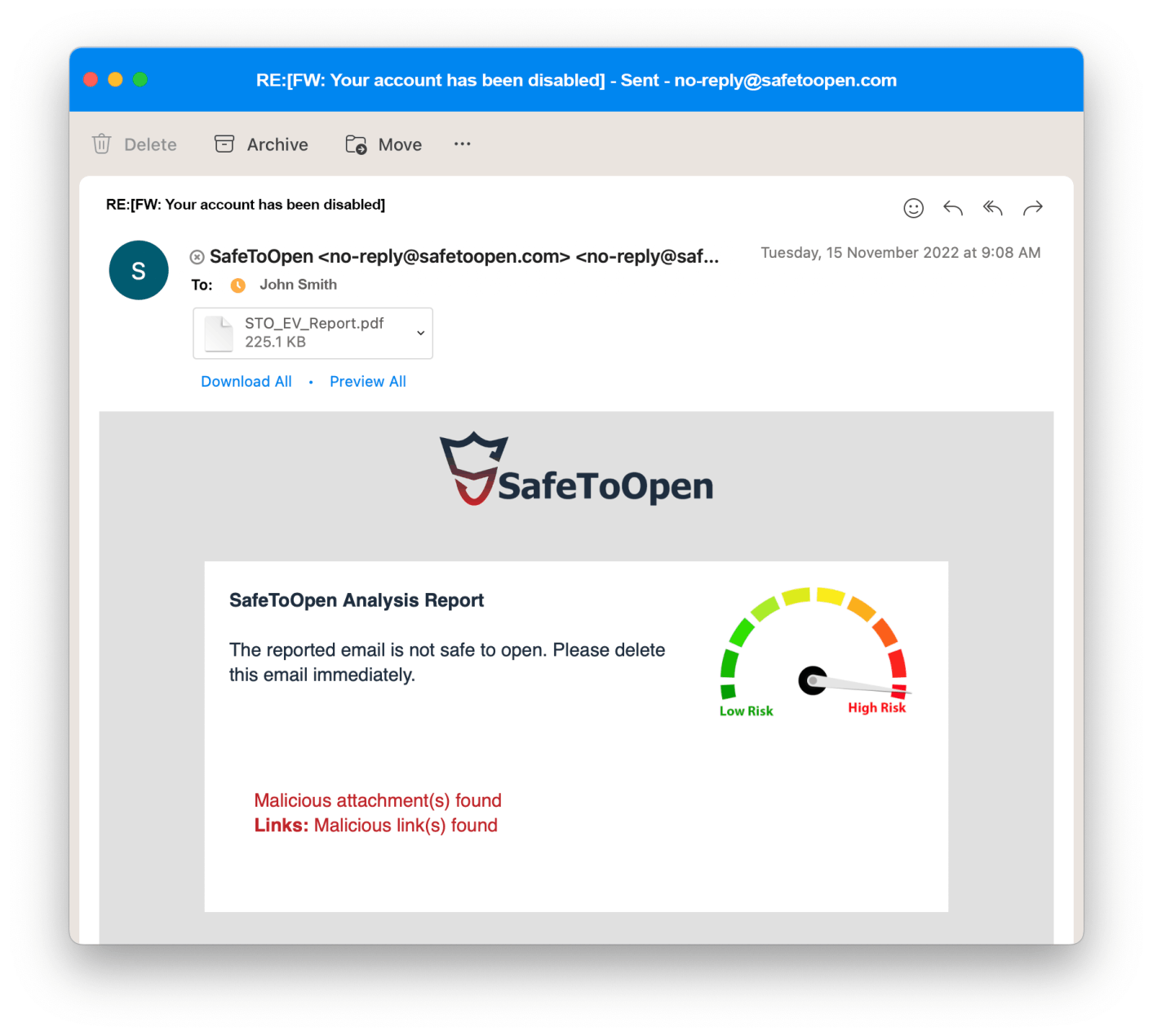
Because SafeToOpen Email Verification only verifies the reported emails and some staff members may forget to verify their suspicious email, we strongly recommend using SafeToOpen Online Security. Ultimately, the phishing links will be opened in browsers, and this is where the SafeToOpen Online Security browser extension can be very effective.
Yes, you can use the same SafeToOpen instance to verify reported suspicious emails.
Yes. You will need to register a new application and provide the necessary permissions to the account you wish to use to verify emails. You can also use separate email addresses for receiving and sending emails.
For example, you can register an application in Microsoft Azure to only read newly reported emails with 'Mail read' permission for [email protected] and register another app to send responses with 'Mail send' permission for [email protected].
SafeToOpen Email Verification also supports the legacy secure IMAP and secure SMTP protocols.
SafeToOpen will provide a step-by-step documentation to set up and configure the SafeToOpen Email Verification.
Yes. You need to register a new application and provide necessary permission to the account you wish to use to verify emails. You can also use seperate email addresses for receiving and sending emails.
For example, you can register an application in Microsoft Azure to only read newly reported email with 'Mail read' permission for [email protected] and register another app to send responses with 'Mail send' permission for [email protected].
SafeToOpen Email Verification also supports the legacy secure IMAP and secure SMTP protocols.
SafeToOpen will provide you with a step-by-step documentation to set up and configure the SafeToOpen Email Verification.